Portable USB drives—the kind based on 2.5″ hard disk that you can slip in your pocket—have always been a huge convenience if you use more than one computer in different locations. But they’ve often struck me as problematic in several ways.
- Small rotating drives don’t travel well. Drop them more than a few inches while they’re in use and your data could be toast.
- Yes, rotating drives are considerably cheaper per gigabyte than USB sticks but the gap is closing. But do you really want to carry a terabyte of data around with you?
- Those data may be business-sensitive. What happens if you lose the drive?
- Cloud-based services like Dropbox or the remote access provided by today’s NAS manufacturers make it largely unnecessary to carry data physically around from place to place.
It’s understandable that if you’re nervous about that penultimate point you probably won’t want to go the Dropbox route either. Trust in your Cloud provider is an act of faith; from a pure engineering point of view, even if you’re reaching over the Internet to your own NAS, you can have no idea who may be eavesdropping on your data. We recently discovered, for example, that our conversations with Amazon’s Alexa are routinely being shared with Amazon employees.
So what we’re looking for is a personal portable hard drive that won’t mind too much if it’s knocked about a bit, doesn’t encourage us to pump it full of too much sensitive data, and if it gets lost—too bad for the finder because the data will be inaccessible.
How does the iStorage diskAshur PRO2 shape up to this task?

I HAVE TO START BY CONFESSING I dislike the logo for this thing. The manufacturer probably means to convey that it’s a disk that “assures you”, with “PRO” added to distinguish the product from their uncertified range.
Why the “PRO” has to be in caps, I don’t know. The 2 I’d assume indicates that it’s the second generation of the product but is probably added here as a superscript to give the thing a scientificky feel. The lock symbol doubling as a capital “A” is clever, but the idea is visually messed up by that superimposition of a lower case “a”.
It’s a good job we’re not here to discuss graphic design aesthetics.
So let’s talk about what it does. A lot, in fact. Drawing a few hundred milliamps of current over a USB 3 data connection to your computer, it becomes a mil-spec encryption machine.
Once plugged in, the drive will need decrypting before you can write to it or access the data. Input for the codes is through a numeric keypad, 0-9 with three additional keys for Lock, Unlock and Shift.
There’s no display screen—you get feedback solely from a combination of three red, green and blue LEDs.
Initially…
The iStorage specification tells us this is:
the world’s first and only NCSC CPA, FIPS 140-2 Level 2/3, NLNCSA BSPA and NATO restricted level certified encrypted portable hard drive.
A lot of initials. Let’s look into that.
US-style, military-sounding specifications are bandied about rather loosely in the computer industry but that’s not the case here. CPA stands for Commercial Product Assurance, a certification awarded by the UK’s National Cyber Security Centre (NCSC).
With FIPS, the Federal Information Processing Standard, we cross the Atlantic to the US and Canada. As the name implies, these are benchmarks that formally validate the cryptographic effectiveness of an item of hardware. There are four levels of FIPS, so the security of the diskAshur PRO doesn’t extend to the highest requirements. But it comes close to level 4 by enabling auto-destruction of your data if the device detects persistent attempts to brute-force the password.
- Level 1 Requires production-grade equipment and externally tested algorithms
- Level 2 Adds requirements for physical tamper-evidence and role-based authentication. Software implementations must run on an approved operating system.
- Level 3 Adds requirements for physical tamper-resistance and identity-based authentication. There must also be physical or logical separation between the interfaces by which “critical security parameters” enter and leave the module. Private keys can only enter or leave in encrypted form.
- Level 4 This level makes the physical security requirements more stringent, requiring the ability to be tamper-active, erasing the contents of the device if it detects various forms of environmental attack.
These are impressive—and more importantly—real specifications.
What do I have to do to make the diskAshur work?
 Are you good at remembering numbers? I’m maths phobic myself, and there is nothing like a string of numbers to send shivers down my spine.
Are you good at remembering numbers? I’m maths phobic myself, and there is nothing like a string of numbers to send shivers down my spine.
At first glance it seems you only have the option to enter numbers on the diskAshur keyboard. But on careful inspection you’ll notice that the keys marked 2 to 9 also carry a set of alpha characters, like a landline phone.
The Quick Start Guide doesn’t mention this, but the full manual (discussed below) suggests that innumerates like me can use this to create easily memorable passwords.
For the purposes of this review I stuck strictly to the default admin password that comes with every sample of this device. The default is also listed in the online manual, and therefore available to anyone in the world.
So, whatever you do, if you’re going to use the diskAshur as it’s intended, the first thing is to change that password.
And you’d better remember that password, too…
Unless you know the password, your drive is just a chunk of expensive metal covered with a tamper-proof layer of super epoxy resin in a rather classy zippered carrying case.
If you’re unsure of your password you have five chances to get it right before you’ll have to disconnect the drive and then plug it in again for another five attempts.
If those fail, it’s probably time to panic. You can get another batch of five attempts by holding down the shift key next time you plug the drive in. But then it’s the end of the line.
If you’ve messed up all 15 attempts you’d better hope you’ve got a backup somewhere. Because “On the fifteenth consecutive incorrect PIN entry, the diskAshur PRO2 assumes it is being attacked and will delete the encryption key and lock itself, rendering all data previously stored on the drive as lost forever. At this point the drive can be reset to factory default settings and redeployed.”
So the thing isn’t actually going to go up in smoke, in the tradition of the original Mission Impossible series. Which means that any would-be thief is still left with a useful acquisition because the rules for resetting it and starting all over again with a fresh drive are freely available on the Internet.
Diving Deeper
If it’s security you’re after, there’s plenty more of it. So far we’ve only touched on the basics covered in the skimpy Quick Start Guide that comes in the package. The full manual is included as a pdf on the drive or you can download it from the Web. You’ll need to read it to discover the rest of the diskAshur story.
This is where I found iStorage’s suggestion about how math-blind people like me can use the keyboard alphanumerically to create passwords that are easy to remember.
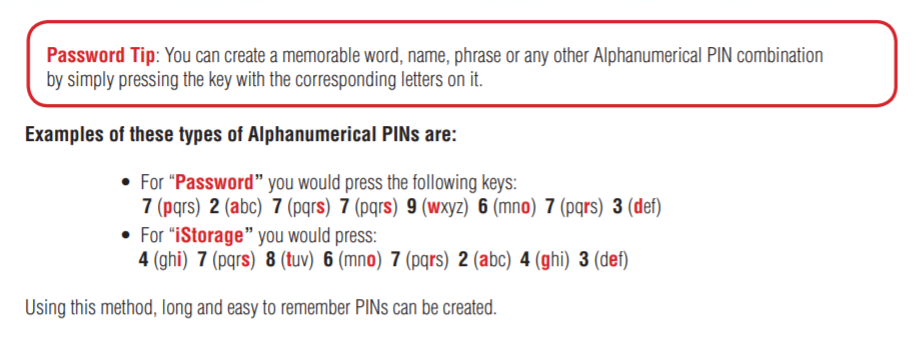
I’m not convinced this leaves me any better off, particularly as the blue characters aren’t easily visible except in really good light. There’s a further level of password complication: you can use the shift key in conjunction with any of the number keys. I suppose this could work for some people—”Password” with a capital “P” being translated as “Shift-7 2 7 7 9 6 7 3”.
That’s an added level of complication for any would-be cracker. But also an added level of complication for me to remember. The one thing I can manage to remember is that after 15 goes you’ve lost all your data. Which is why, for the purposes of this review, I’m sticking with the default admin password.
The full manual reminds you that a password:
- Must be between 7-15 digits in length
- Must not contain only repetitive numbers, e.g. (3-3-3-3-3-3-3)
- Must not contain only consecutive numbers, e.g. (1-2-3-4-5-6-7), (7-8-9-0-1-2-3-4), (7-6-5-4-3-2-1)
Night Train to Novgorod
Your company notebook has gone. But that’s ok—no sensitive data on that. But the diskAshur? Still wired to the notebook, still powered up, so…
But you’re fine. You’ve learnt from the full manual how to set up a time-lock. By the time the thieves get to somewhere where they can sit down and assess their winnings, the diskAshur, even though still powered, will have gone into lockdown mode again.

While the thieves are wrestling with the passcode, they’re captured in a police raid. That evening you get your laptop and your diskAshur back and check to find that the data’s all intact just in time to meet your colleague at the station and catch the train.
Over dinner, as the train hurtles Eastward, your colleague tells you she’s got some sensitive data she needs to store but doesn’t have her own diskAshur. You’re happy to help her out with some of your disk space but you don’t want to share your password. You’ve been warned she may secretly be working for a rival company.
You could set up a separate user password for her. This will give her access to the drive without admin privileges, so she won’t be able to change any of the security settings.
But because the diskAshur security system is completely independent of the file system it has no way of restricting her access to your own files. Never mind. You ask her to give you a couple of minutes…
…and take the time to use Windows’ own encryption to lock down your private folders against a separate password. Once unlocked, the diskAshur drive behaves like any other Windows drive so you have no problem applying whatever secondary encryption you might choose. Now you can create a diskAshur user passcode for her and let her share the drive.

Dawn is breaking as you arrive at the border, where a suspicious-looking security guard insists you give him the diskAshur admin passcode. You’ve caught the look between him and your colleague and reckon there’s a chance he may be in on it too. After an exchange of sharp words he takes his gun out of his holster and puts it on the table to remind you who’s in charge.
Under protest, you scribble a string of 15 digits on a piece of paper and slide it over to him. He plugs the drive into his laptop and types in the numbers.
The drive turns out to be empty. Not a file or folder to be found. Unformatted, in fact. You had the foresight at the beginning of your trip to set up an autodestruct code.
Appendices A &B
At the end of the full manual, under Appendix A, you’ll find a document called “iStorage Security Directive #1”
Aimed at commercial, public service, and government agency users, the document sets out the official advice from GCHQ about digital security. It’s an important reminder that security isn’t just about technology and simply pressing a bunch of buttons is never all you need to get the job done. Human behaviour and processes around the technology are also—perhaps even more—important.
Appendix B, iStorage Security Direction #2, relates to subsequent disposal of the diskAshur drive once you’re done with it. Even if you’re not 007 or otherwise charged with the responsibility for eyes-only information, the two appendices are worth a read. If you’ve taken the trouble to invest in a diskAshur drive, or been issued one by your organisation, you’re probably the sort of person who should be mugging up on this stuff.
Protection Money
 If you value the security, you may feel (as I do) that the strict defence system of the diskAshur PRO2 more than justifies the £200ish price of the 500GB SSD version under review here.
If you value the security, you may feel (as I do) that the strict defence system of the diskAshur PRO2 more than justifies the £200ish price of the 500GB SSD version under review here.
It’s true that you can pick up a raw internal SSD that’s four times the size for that same price. I calculate that you’re paying a premium of about £150 for iStorage’s unique selling proposition. If gigabytes per buck is your sole consideration clearly the diskAshur PRO2 is not for you.
Hollywood might be able to justify the £2,000+ price of the 8TB diskAshur Pro2 as a useful way of distributing movies to cinemas.
You can split the difference with some of iStorage’s less pricey offerings. The hard drive version in the same 500GB size comes in a little cheaper at around £160. Or you could go for the 64GB datAshur Pro 64GB USB stick for forty quid less. These all include the same security features.
What we’ve got here is a sturdy, fast, thoroughly documented portable drive designed and assembled in the UK. It offers first-class security and comes with a two-year warranty. If data you’re moving about is worth protecting, this is the way to do it.
In this context, please also see this thank-you to our Web host.
Chris Bidmead
